Imagine you have a super-powerful lock protecting all the Bitcoin in your digital wallet.
Right now, no ordinary computer can break that lock in any reasonable amount of time. But quantum computers aren’t “ordinary.”
They use a whole different kind of math and computing power.
The Promise of Quantum Computing
Quantum computing has long been a source of excitement for researchers.
Unlike traditional computers that use binary digits (0 or 1), quantum computers leverage qubits, which can exist in multiple states simultaneously—thanks to a principle called superposition.
This unique capability allows quantum processors to handle exponentially more data in parallel than classical machines.
- Breakthrough Potential:
From optimizing global supply chains to modeling complex molecules for drug discovery, quantum computing promises game-changing solutions to previously intractable problems.
- Cryptographic Threat:
Unfortunately, the same power that lets quantum devices solve huge puzzles also poses a significant risk to current cryptographic standards.
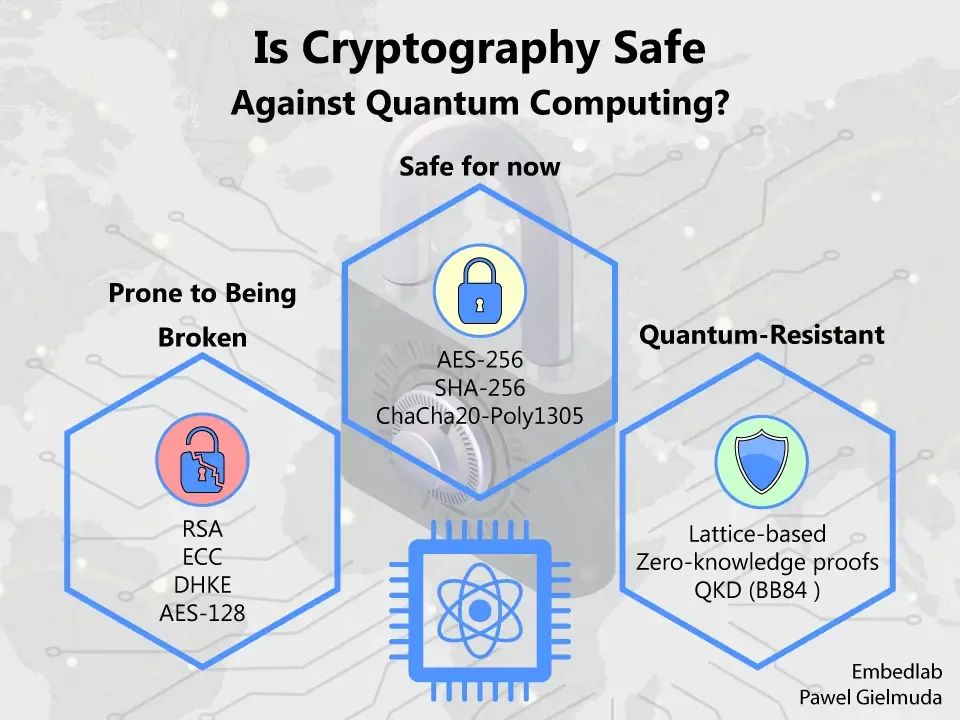
This includes the elliptic curve cryptography (ECC) widely adopted by Bitcoin, Ethereum, and many other blockchain networks.
Below, we’ll look at the specific ways quantum computers might one day hack or tamper with Bitcoin.
1. Cracking Private Keys
How Bitcoin Wallets Work:
- Public Key: This is like your mailing address. You share it so others can send Bitcoin to you.
- Private Key: This is like the key to your house. Only you have it, and it lets you actually spend (send) your Bitcoin.
Today’s Security:
Regular computers can’t easily figure out your private key just from your public key. Doing so would take them longer than the age of the universe.
This is because Bitcoin relies on a type of math called elliptic curve cryptography, which is extremely difficult to crack with conventional methods.
Quantum Threat:
Quantum computers can potentially use algorithms (special math shortcuts) to solve these tough problems much faster.
One famous example is Shor’s algorithm, which can, in theory, uncover private keys by crunching through elliptic curve math in a fraction of the time.
Why It Matters:
If a quantum computer can figure out your private key from your public key, it could move your Bitcoin anywhere it wants—without your permission.
2. Faking Signatures (Transaction Tampering)
When you send Bitcoin, you “sign” the transaction with your private key to prove you’re the owner. Nodes on the Bitcoin network check that signature before approving the transaction.
Today’s Security:
No one can forge your digital signature without knowing your private key. That’s why transactions today are trustworthy.
Quantum Threat:
If a quantum computer can calculate private keys or break the signature system, it could:
- Forge Signatures: Spend Bitcoin from any address without the real private key.
- Disrupt the Network: Potentially create false transactions and cause massive confusion.
In other words, quantum computing could flip the basic trust mechanism in Bitcoin on its head.
3. Altering Past Transactions
Blockchain Basics
Bitcoin transactions are gathered into “blocks,” which are then chained together. Each block is like a page in a ledger, and each page depends on the previous one.
Altering old transactions means you have to rewrite a part of the blockchain’s history—something that’s nearly impossible with classical computers.
Why It’s Difficult Even for Quantum
To rewrite the past, a hacker must re-mine every block after the one they change (this takes immense computing power and also requires competing against all other miners).
Possible “51% Attack” Edge
With a quantum advantage, a single entity might gain the majority of the network’s mining power (a “51% attack”). This could let them rewrite recent blocks if they’re extremely lucky and well-equipped. While not the easiest method, it’s still a concern if quantum machines become powerful enough to outrun regular miners.
4. Speedy Key Searching
While Shor’s algorithm gets most of the spotlight for cracking elliptic curve crypto, there’s another quantum algorithm called Grover’s algorithm that speeds up searching.
Practical Concern:
Grover’s algorithm doubles the speed of brute-force searches, but doubling speed alone might not be enough to instantly break Bitcoin addresses with strong encryption. However, combined with other improvements, it might still pose a risk over time.
The Real Quantum Dangers
-
Private Key Extraction: A quantum computer could figure out your private key from your public key, letting an attacker steal your coins.
-
Forgery of Transactions: By breaking Bitcoin’s digital signature system, hackers could forge transactions and cause chaos in the network.
-
Potential Blockchain Rewrites: While very tough, a quantum “super-miner” might attempt to rewrite parts of the blockchain if it surpasses the rest of the network in mining power.
-
Speedy Searches: Advanced quantum algorithms could brute-force private keys in far less time, making once-impossible hacks a real possibility.
The Road Ahead

Quantum computing’s potential, illustrated by advancements like Google’s rumored “Willow” chip, highlights the urgency for blockchain networks to evolve. Bitcoin and similar systems currently rely on cryptographic safeguards that may be at risk as quantum technology advances.
Possible Mitigations in a Post-Quantum World
-
Quantum-Resistant Algorithms: Researchers are developing and testing post-quantum cryptography, including lattice-based and hash-based signature schemes, which are believed to withstand quantum attacks.
-
Secure Key Management: Rotating addresses and employing multi-signature wallets that use post-quantum keys can significantly reduce exposure to potential key cracking.
-
Gradual Transition: By adopting quantum-resistant features early on, the industry can avoid a large-scale security crisis when truly powerful quantum computers become mainstream.
Ultimately, the vulnerability of Bitcoin and blockchain to quantum threats—and how dire that vulnerability becomes—will hinge on the speed with which they adopt robust, quantum-resistant solutions.







